Additional Options
Encryption of Communication Instances
This feature provides the possibility to encrypt the configuration files of Communication Channels used by the Instance, which may contain credentials to access a database or external services. The encryption method used is Advanced Encryption Standard (AES).
The encryption is available for all deployment options, by following the steps bellow:
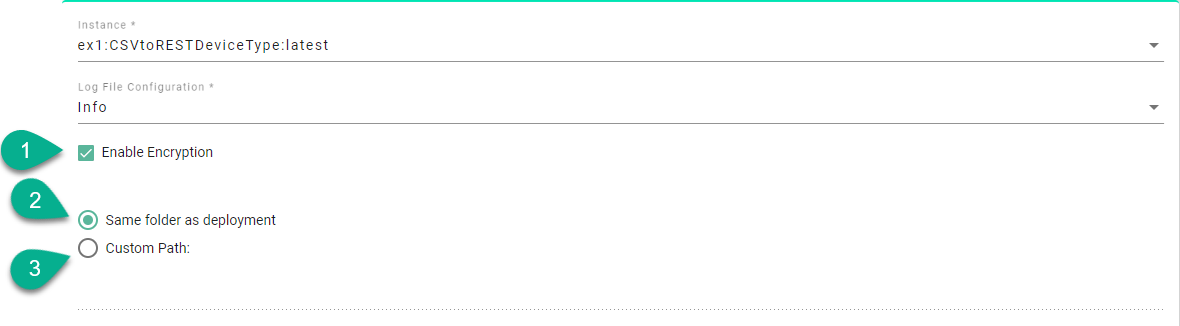
Check the Enable Encryption box (1).
A symmetrical key (cfg.key) is generated and can be saved in the same folder as the deployment (2) or check the Custom Path option (3) to save the key into a secured location.
Protect Communication Instances
This feature provides an additional protection when performing an Instance action (e.g., deploy, undeploy, start, stop).
The protection is available for all deployment options, by checking the Protected box (1).

Now the Instance is protected, meaning that when the user performs an action like Deploy (2), a popup appears requiring to input the Instance name (3).

Note
Protected Instances will not work with Bulk actions.
VM Arguments
This feature provides the possibility to configure the Java Virtual Machine (JVM). In some cases, when dealing with larger files when using the File Reader Communication Channel (large XML file), it might be necessary to increase the XMX in order to avoid running into a java.lang.OutOfMemoryError - exception.
VM Arguments can be configured when deploying an Communication Instance locally or on Docker, by following the steps below:
Check the JMX Properties box (1) to expand the Java Management Extensions parameters and input the JMX Host Name and Port (2).
Check the authentication method (3).
Update the XMS value (4), minimal heap size, representing the amount of memory used by the JVM to start with.
Update the XMX value (5), maximal heap size, representing the maximum amount of memory that JVM will be able to use.

By default, the Heap Dump On Out Of Memory Error option is checked, providing an analysis file for debugging.
Additional JVM arguments can be added by selecting the add Arg button (6) and input the argument (7). For example, to debug memory issues or application performance, the Garbage Collection logging can be enabled in JVM, as seen below.
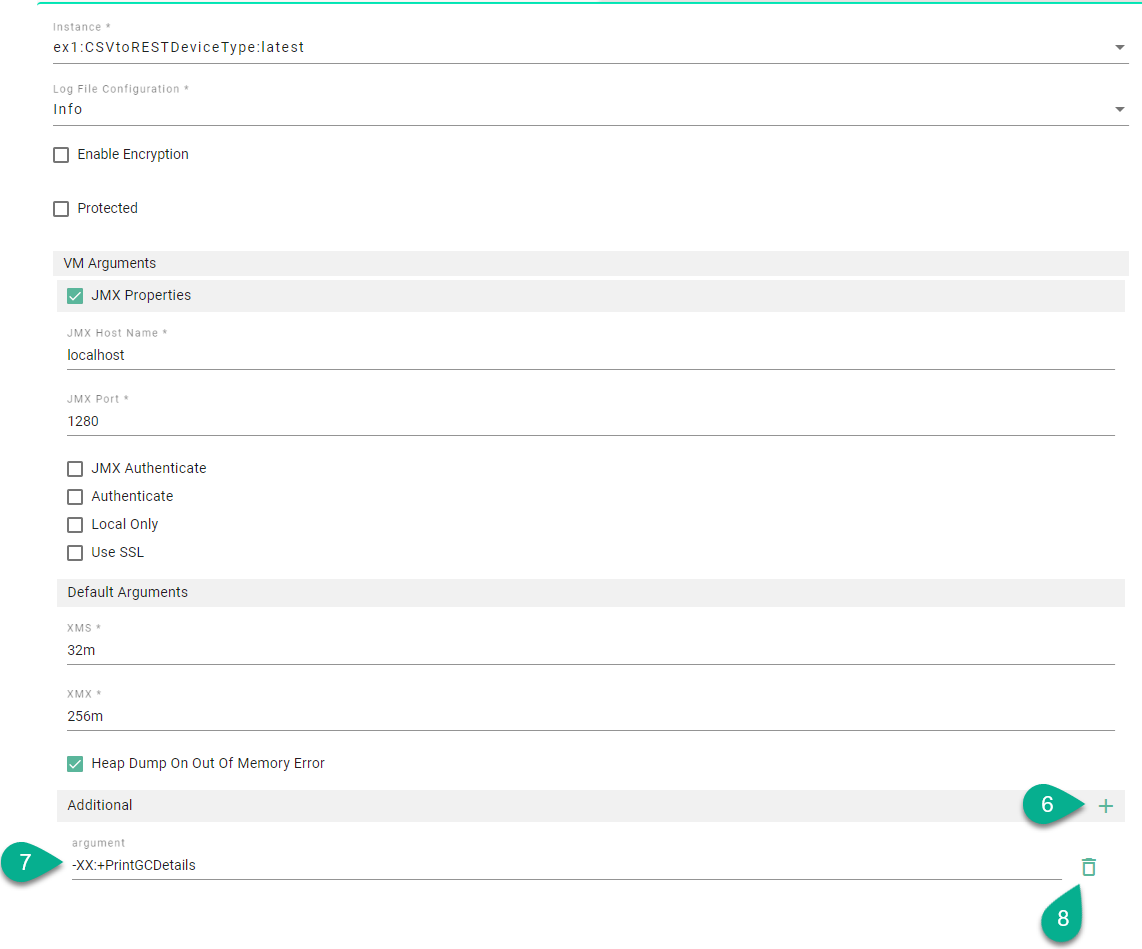
An additional argument can be deleted by clicking on the delete Arg button (8).